Over the last few years, Cequence has seen a trend of larger and increasingly distributed attacks. In 2024, Cequence identified and blocked one of the largest application business logic abuse attacks on record. These massive attacks often coincide with common holidays such as Black Friday and the Christmas shopping season. The latest large-scale attack Cequence has detected and blocked coincided with Valentine’s Day and was a huge botnet distributed over an astonishing nine million IP addresses.
Anatomy of the Attack
Residential proxy networks were used to carry out the attack against a Fortune 500 hospitality company. The attack features credential stuffing, meaning attackers attempted to brute force their way into legitimate user accounts at the target business, usually with username and password pairs harvested from prior data breaches. Credential stuffing can be a successful tactic, especially at scale, since many users reuse their login and password across internet accounts.
Attackers focused on the company’s login systems to identify active accounts, at which they would have access to the legitimate user’s payment information.
This attack was highly distributed, scaling to over nine million IP addresses, making traditional attack mitigation systems that rely on IP addresses for blocking, such as a WAF, impotent. The attack also leveraged residential proxy networks to make blocking by IP more difficult and used proxy pools that are in the same country as the company’s main user base to further mimic legitimate traffic. The target company typically sees increased seasonal traffic in mid-February, coinciding with Valentine’s Day, and the attacker was likely attempting to hide their malicious traffic in the higher legitimate traffic volumes.
The following chart depicts attack events by country:
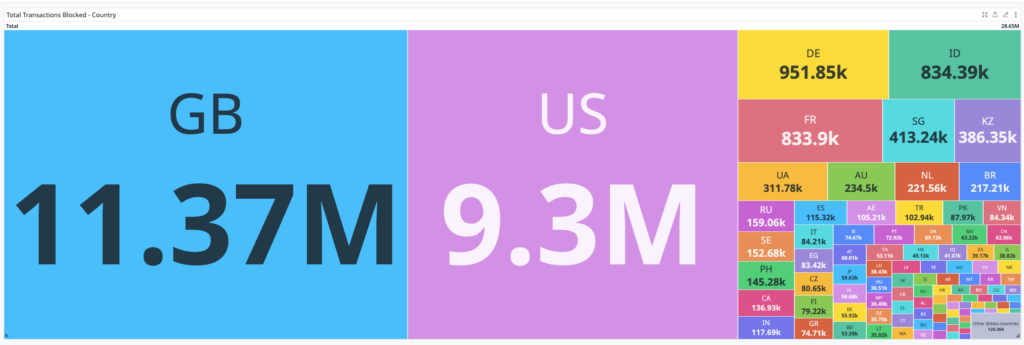
This chart shows unique IP addresses used in the attack by country of origin. The vast majority of the traffic originated in the UK (Great Britain), which is also where the target company is located.

The chart below shows how the attacker spread the attack across a large number of ISPs, with a substantial amount originating from Optibounce.

Attack Sources
Devices used in the attack were primarily compromised routers and IoT devices, which is consistent with the botnet makeup Cequence usually sees in these types of attacks. The attack generated over 28 million total security events, resulting in approximately 3 events per unique IP address.
Attack Detection
Instead of IP-based detection, Cequence’s unique fingerprinting technology identifies attacks based on behavior and other criteria to detect both high volume and “slow and low” attacks with high accuracy. Cequence’s fingerprinting algorithm relies purely on server-side intelligence analyzed by machine learning models. In this attack, even though the source traffic was widely distributed across more than nine million IP addresses, Cequence identified the attack with just one fingerprint.
Attack Prevention
Unlike other bot management solutions, Cequence requires no client-side instrumentation such as JavaScript or mobile SDKs. The benefits of this approach are many:
- You don’t have to instrument each application you want to protect, such as adding CAPTCHAs
- You can protect APIs as well as applications, as APIs don’t support JavaScript-based approaches
- All applications and APIs whose traffic is seen by Cequence are protected
Cequence offers ML-based policies that can block malicious traffic based on fingerprints, whereas legacy bot management solutions rely on IP addresses and would clearly fail to prevent this large-scale attack. Cequence was able to easily mitigate this attack due to its unique fingerprint technology. A single fingerprint was identified as malicious, and blocking the entire attack took only a single policy. No IP address list was required to be uploaded into the system, and as the attacker changed infrastructure to attempt to evade detection, Cequence continued to block them.
Summary
This attack is unprecedented in its scale against this particular target application in a short time period, but Cequence excels in mitigating attacks of this nature and does so on nearly a daily basis across its customer base. Each day Cequence mitigates over 327 million credential-stuffing events, or about 10 million events, across its customer base which saves approximately $6.3M in account value per month. Contact us to learn how Cequence can help protect your business against credential stuffing bot attacks and much more.
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.




