A large telecommunications API security customer with over 100 million mobile subscribers detected and blocked a sophisticated API-based phishing attack in a matter of hours, highlighting a rapid API security time-to-value provided by the Cequence Unified API Protection (UAP) solution.
With many applications that support their mobile business, their IT security team is constantly on the look-out for cyber-attack campaigns that seek to exploit their mobile users via theft and fraud, often taking advantage of stolen personal data. The attackers had built a series of fake websites mimicking the company look and feel to attract users and steal data.
Sophisticated Phishing Campaign Outmaneuvers API Security
In a recent attack, the security team discovered a sophisticated phishing attack campaign that targeted their customers and their mobile devices asking them to change their password. The attacker created a set of fake malicious sites that could interact with the carrier’s API application used to authenticate these mobile users. The attacker positioned these malicious sites as a fake middleman between the mobile user and API application. Once the mobile user clicked on the URL in the phishing email, the attacker’s malware site redirected them to an API application verifying the identity of the user via multi-factor authentication (MFA). Once authenticated, the malware site presented the mobile user with a fake webpage, which was an exact replica of the mobile carrier’s change password webpage, except for the URL which closely resembled the carrier’s domain. The mobile user would insert their credentials, thinking they changed their password when in fact they had unknowingly provided their username and password to the attacker. Once compromised, the cybercriminal was able to access the mobile user’s account and purchase a new iPhone by establishing a new phone line without the account owner’s consent, costing the carrier anywhere from $1000 to $1500 per compromised account.
The attack is a perfect example where an API security program can help ensure that APIs follow the right specifications to minimize losses due to API vulnerabilities. But much more is needed because in his case, the APIs were not necessarily coded or configured incorrectly. A more unified approach for API protection is required that also protects from the most sophisticated and relentless attacks that use legitimate traffic to commit theft, fraud, and cause business disruption.
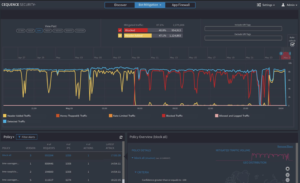 Cequence Security API Spartan in Action: Detection and Mitigation.
Cequence Security API Spartan in Action: Detection and Mitigation.
API Spartan Helps Provide API Protection and Disrupts Major Cyber Campaign
The application security team understood that they had a severe problem. With API Spartan a component of the Cequence UAP solution, they were able to quickly onboard API protection to mitigate the targeted attacks. The security team had jumped on protecting this API application used to verify the identity of users by implementing protection in under 30 minutes. The security team placed API Spartan in front of this API application that intercepted all redirected requests from 3rd party sites such as from a search engine or, in this case, malicious or fake websites. Through API Spartan, they were able to develop new security policies that were able to distinguish between legitimate versus malicious redirects, enabling them to block all rogue requests, that originated from over 75 malware sites. In a matter of days, this complex and sophisticated cyber-attack campaign was completely stopped right in its tracks. The attacker gave up the campaign soon after.
Free Telecommunications API Security Assessment of Your API Attack Surface
Get an Attacker’s View into Your Organization
Sign up for the latest Cequence Security news
By clicking Subscribe, I agree to the use of my personal data in accordance with Cequence Security Privacy Policy. Cequence Security will not sell, trade, lease, or rent your personal data to third parties.